It’s no secret that consumers with a water, gas, or electricity connection have long been targets for utility scams, and in today’s increasingly digital world, cyberattacks are, unfortunately, nothing new. In this article, we will discuss some common types of attacks cyber criminals use and how to defend against them.
The Attacks
Cyber criminals can attack on a multitude of levels, from large-scale attacks targeting corporations to smaller phishing attacks aimed to gain an individual’s personal information.
Imposter scams are the #1 type of fraud reported to the Federal Trade Commission. Scam artists may contact you by phone or even come to your door posing as a utility worker for your local power, water, gas, or even phone and TV company. The scammer may claim you are overdue on your bill and threaten to disconnect your service if you don’t pay immediately. Whether this is done in person or by phone, the scammers want to scare you into making an immediate payment, so you don’t have time to think clearly. This can also appear in the form of a computer pop-up (usually claiming to be from Microsoft) complete with a voice urging you not to even shut down your computer. This particular “Scareware” tactic can be intimidating if you’re not careful.
Second, scammers may also send emails claiming to be a shipper such as Amazon or USPS holding a package claiming they need more information in order to deliver it. They may send you a “Thank you for your order” email for something you didn’t order, suggesting that if it was in error to contact this number/email. They might include very convincing formatted email forms with logos and everything. Impersonating payment services like PayPal is another big one.
Thirdly, while negative reinforcement-based tactics are common, not all scammers use them. Some scammers may falsely claim you have been overcharged on your bill and say they want to give a “refund”. It sounds easy. All you must do is first provide information to “prove” they have the correct person on the phone or click/press a button in an email to initiate the process. If you proceed, you will be prompted to provide banking or other personal information. However, instead of money going into your bank account, scammers can drain your account and use personal information such as a social security number (even a partial) for identity theft.
Defend Yourself
So, how can you defend yourself against a scammer? First, awareness is key. If you are on the lookout for unknown or strange callers claiming they are from somewhere you don’t hear from often, don’t be afraid to question the presenter and keep your guard up until you can verify what’s going on.
Second, if you find yourself in a situation and it’s a call, hang up; no matter what they say to keep you on the line. The IRS doesn’t call you to then send the sheriff/police after you. If it’s an email, you must resist calling any numbers or clicking on any links provided in these messages. If it’s in person, and most importantly, never let anyone into your home that you don’t know unless you have a scheduled appointment or have reported a problem. When in doubt, contact your provider to verify the presence of personnel. Then keep the following in mind:
- Know that phone scammer’s caller ID can be faked (or “spoofed”) to look legitimate, or it may simply just lead right back to them.
- Contact the company directly yourself from the known contact number stored in your phone or look it up on the internet. For email, go to the provider’s site directly from a bookmark/favorite or by typing in the company’s name into your web browser
- Don’t provide your banking or other account information as “verification” to an unsolicited caller or email website link… No matter what they claim.
- Most legitimate companies who issue regular monthly bills will not contact you to issue a “refund” but instead will usually just credit your account towards the next bill.
- Emails and texts that indicate financial transactions that are suspicious should be followed up with your bank/card issuer to verify a charge has actually happened before you contact the company. When you do, use known official methods outside of the email sent to you.
Safeguard Yourself
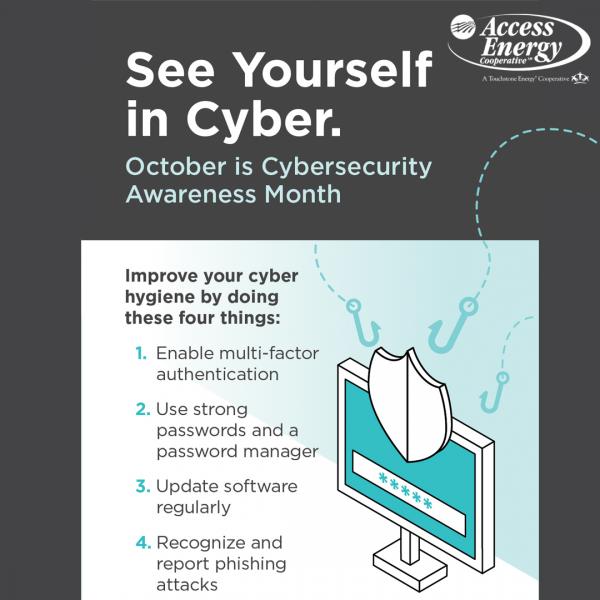
You may ask “What can I do to help safeguard my digital life?” The truth is that there are several practical steps we can take to safeguard our devices and data. We call it “Cyber & Digital Hygiene.”
- Enable Multi-Factor Authentication: This is also known as Two-Factor Authentication or 2FA. This adds an additional step when accessing sensitive data (such as bank accounts) to prove you are really you and not someone trying to impersonate you. This extra step could include an extra PIN, a security question and answer, or a rotating one-time password (OTP) token. Regardless of the method, this additional step makes it many times harder for cyber criminals to access the same information or account. If you’re not sure, contact your bank/utility/business entity, and if it’s available, activate it and use it.
- Use Strong Passwords & A Password Manager. If it’s relatively easy to remember, it’s not secure. Remember, passwords are the “keys” to your life in the digital world. Simple passwords like family/pets names with a couple of numbers aren’t necessarily secure. Also, you wouldn’t want the key of someone’s house down the street to be the same as yours, right? Not to mention you wouldn’t use the same key for your house as you do your car, right? Your passwords should always be long, unique to the service, and complex. Passwords for sensitive accounts should be at least 12 characters, don’t re-use them on multiple services, and use complex combinations of upper/lower case letters, numbers, and special characters. If you need help doing this or find it hard to remember them, there are several password manager programs out there, including ones that are free. You use one memorable password to activate it, and it can create, remember, and automatically fill in the more complex ones for you.
- Recognize Phishing/SMShing Attacks. Cyber criminals will try to get you to click on things or divulge personal identifying information. This is called “Phishing” (like fishing) when it’s by email and “SMShing” (smishing) when via text messages/SMS. Don’t take the bait. The signs of a Phishing/SMShing campaign can be subtle, but most offer too-good-to-be-true scenarios. Also, any communication that has an urgent or alarming tone, misspellings, poorly-crafted language, ambiguous greetings, and strange requests (like purchasing gift cards) has a high potential to be illegitimate. They will also come from an email address that doesn’t match the company they’re trying to “represent”.

